

While the NIS2 directive primarily affects EU member states, its implications extend beyond the EU, including the UK. Many UK companies collaborate with EU-based organisations or operate across borders, making compliance with similar cybersecurity frameworks essential. Moreover, adopting a multi-layered cybersecurity approach, as highlighted in this article, is a best practice that enhances overall resilience against cyber threats, regardless of geographic location.
As the cyber threat landscape continues to evolve, the sophistication and frequency of attacks are escalating at an alarming rate. This is particularly concerning for small to medium-sized businesses (SMBs), which are often perceived by cybercriminals as easy targets. With the upcoming enactment of the NIS2 Directive in October, organisations in Ireland and across the EU must reassess their cybersecurity strategies to ensure compliance. The NIS2 Directive, which builds upon the original NIS Directive, introduces stricter requirements for cybersecurity across critical sectors. This makes adopting a robust multi-layered approach to cybersecurity not just advisable but essential.
The NIS2 Directive aims to enhance the overall level of cybersecurity within the EU by setting minimum standards for risk management, incident reporting, and supply chain security across all Member States. It applies to a wide range of critical sectors, including energy, transport, health, financial services, water supply, digital infrastructure, and public administration. These sectors are considered essential for the functioning of society and the economy, and therefore they are subject to stricter cybersecurity requirements under NIS2.
Non-compliance with the directive can result in significant penalties, including substantial fines and potential reputational damage. This underscores that cybersecurity is not merely an IT concern but a critical business imperative. The responsibility for compliance under NIS2 rests squarely on each organisation, regardless of size. This means that SMBs must also ensure their cybersecurity measures meet these new standards. With the directive set to be implemented across the EU October 17th, businesses have a limited window to prepare and align their security strategies with the requirements of NIS2.
A multi-layered approach to cybersecurity is not only a best practice but also a strategic necessity in light of NIS2. This approach involves implementing several layers of security across your IT infrastructure, each designed to address different aspects of the cybersecurity landscape. The following sections highlight key areas that should be considered as part of any multi-layered cybersecurity strategy, whether your industry is directly impacted by NIS2 or not.
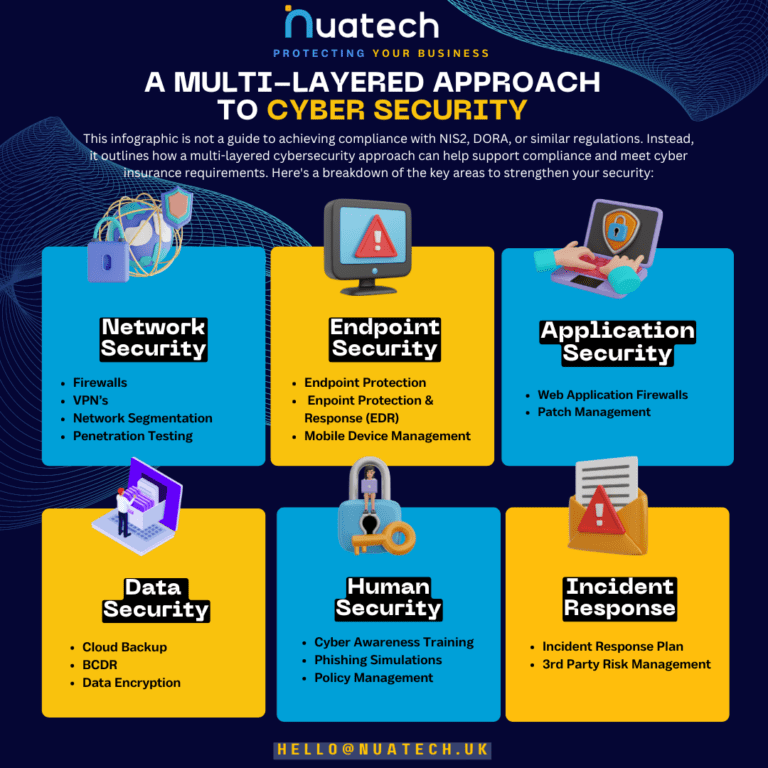
For those looking to explore the specific requirements of the NIS2 Directive in more detail, we recommend reviewing Articles 21 and 23, which cover the essential risk management measures and reporting obligations. Additionally, Recitals 77-85 provide context on the expected cybersecurity frameworks and the emphasis on maintaining a resilient posture across all critical sectors.
You should now conduct a thorough investigation to understand how the incident occurred and what measures can be put in place to prevent a recurrence. This could include strengthening security protocols, improving staff training, or upgrading security software.
As the cybersecurity landscape becomes increasingly complex, and with the NIS2 Directive coming into force, building a multi-layered and robust cybersecurity defence is essential for compliance and protecting your business from evolving threats. Cybersecurity is a continuous process, requiring ongoing monitoring, updates, and improvements. While the responsibility for compliance ultimately lies with your organisation, partnering with Nuatech can provide the expertise and solutions to help you strengthen your defences and achieve compliance with NIS2. Get in touch with us at hello@nuatech.uk to see how we can support your cybersecurity journey.