
A recent Business Email Compromise (BEC) campaign has been identified that is using advanced spear-phishing techniques with Adversary-in-the-Middle (AiTM) attacks to target Microsoft 365 accounts belonging to corporate executives. The campaign, which researchers from Mitiga discovered during an incident response case, is now widespread and is targeting transactions worth several million dollars each.
The phishing emails used in this campaign inform the target organisation that their usual corporate bank account is frozen due to a financial audit and provide new payment instructions. These new payment instructions suggest switching to a new bank account owned by a so-called subsidiary, which is actually owned by the attackers. To make the attack more convincing, the attackers hijack email threads and use typo-squatted domains that quickly pass as authentic to CC’d legal representatives known to the victims.
The attack on corporate executives starts with a phishing email pretending to come from DocuSign, the electronic agreements management platform used widely in corporations. The email targets common security misconfigurations often used to limit false positive spam alerts from DocuSign, allowing the email to get inside the target’s inbox. When the target clicks on the ‘Review Document’ button to open it, they land on a phishing page on a spoofed domain, where they are urged to log in to the Windows domain.
The attackers use AiTM attacks to bypass Multi-Factor Authentication (MFA). They appear to be using a phishing framework, evilginx2 proxy, to perform the AiTM attack. When a target inputs their credentials and solves the MFA question, the proxy sitting in the middle steals the session cookie generated by the Windows domain. The attackers can now load the stolen session cookies into their own browsers to log into the victim’s account and bypass MFA automatically, which was verified in the previous login. In one of the observed cases, the attackers added a smartphone as the new authentication device to ensure uninterrupted access to compromised accounts remains available to them.
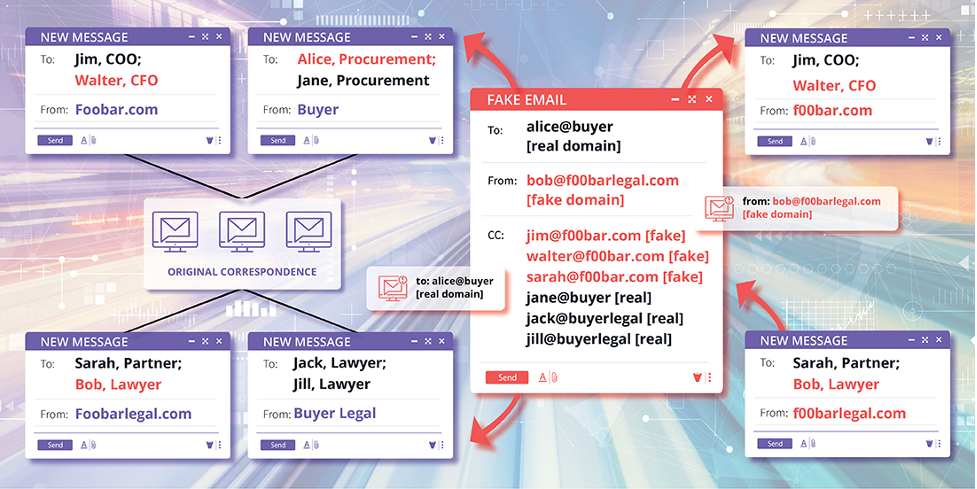
The recent BEC campaign is very sophisticated and displays the technical capability of the attackers behind it. Corporate executives must stay vigilant, and if they suspect any incident, Windows admins are suggested to monitor MFA changes on user accounts using Azure AD Audit Logs. This attack emphasises the need for organisations to ensure that their security systems are properly configured and that employees are trained to identify and report suspicious emails. Additionally, it is recommended that organisations implement measures such as Domain-based Message Authentication, Reporting, and Conformance (DMARC) to prevent phishing emails from reaching their intended targets.