Cyber Security
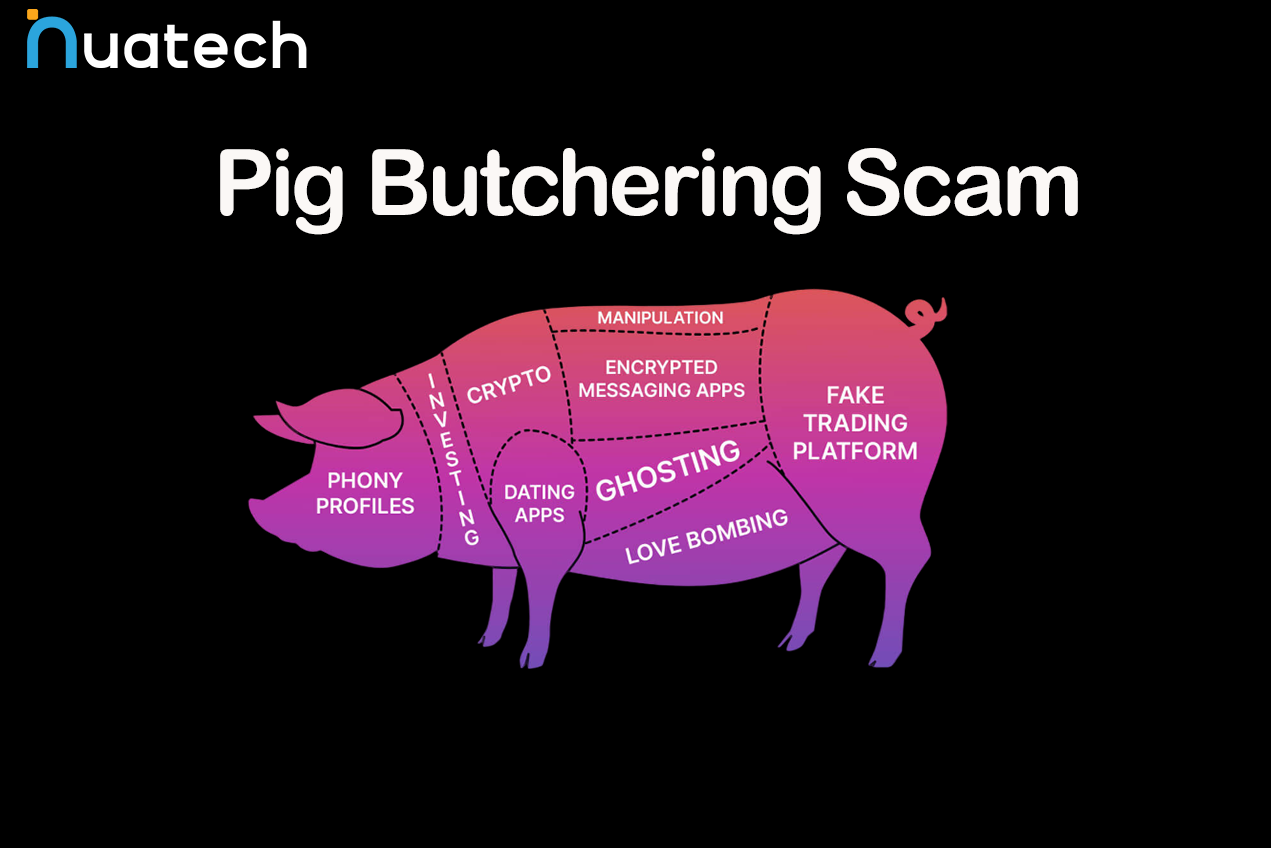
PIG BUTCHERING SCAMS
From business email compromises to romance scams, criminals are raking in billions by using one powerful tool: social engineering. They lure their victims into making

From business email compromises to romance scams, criminals are raking in billions by using one powerful tool: social engineering. They lure their victims into making